Video blocked
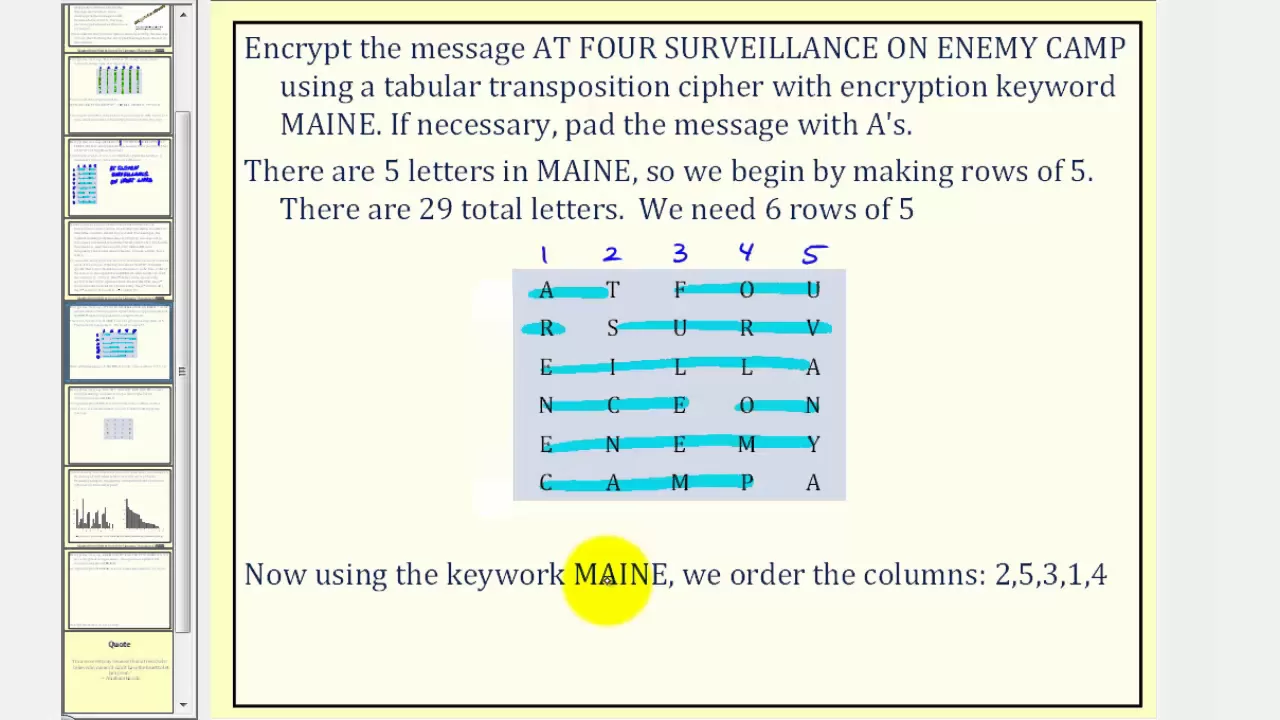

Cryptography: Transposition Cipher
Recommendations
-
02:16 Playfair Cipher
-
09:40 Cryptograph: Substitution Cipher (Caesar Cipher)
-
26:25 The Columnar Transposition Cipher Explained and Broken
-
07:52 Creating An Unbreakable Cipher (nearly)
-
11:25 A visual guide to Bayesian thinking
-
12:49 Playfair Cipher (Part 1)
-
43:15 "The Lost Symbol" - Magic Squares and the Masonic Cipher
-
08:15 How the "Unbreakable" Vigenere Cipher Was Broken
-
08:30 Cryptography: Caesar Cipher With Shift
-
08:14 ADFGVX Cipher: Encryption and Decryption (Updated)
-
08:21 The Science of Codes: An Intro to Cryptography
-
13:25 Double ratchet algorithm: The ping-pong game encrypting Signal and WhatsApp
-
12:55 Hill Cipher Explained (with Example)
-
06:50 What is a substitution cipher?
-
15:26 I did the double slit experiment at home
-
15:37 AES: How to Design Secure Encryption
Similar videos
-
08:15 Row Column Transposition Ciphering Technique
-
02:36 Encrypting using a keyword-based transposition cipher
-
03:58 Transposition Ciphers - Encryption/Decryption
-
02:46 Decrypt using a keyword based transposition cipher
-
06:46 Rail Fence Technique
-
12:33 Cryptography: Crash Course Computer Science #33
-
04:40 Transposition Ciphers
-
07:40 Columnar Transposition Technique Encryption Explained with Solved Example in Hindi
-
03:26 Module 5: What is a cipher (substitution and transposition)?
-
16:34 Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques